
Smart Locks and EN 18031 Certification
en 18031 Overview
As the EU’s mandatory cybersecurity standard for radio equipment, EN 18031will take effect on August 1, 2025, becoming the “entry threshold” for smart locks entering the EU market.
Rather than a single specification, EN 18031 is composed of three sub-standards:
- EN 18031-1: Focuses on network protection, covering defenses against DDoS attacks, encrypted communication, and other connectivity-related security needs.
- EN 18031-2: Specializes in personal data protection, including the secure handling of biometric data and unlocking records.
- EN 18031-3: Targets financial transaction security. Since smart locks typically do not involve payment functions, this standard is rarely applicable.
The key to determining whether a smart lock requires certification lies in two questions:
1. Does the product include a wireless communication modULe (i.e., is it consideRED radio equipment)?
2. Does the product involve network connectivity or the processing of personal data?
Purely wired devices or mechanical-electronic locks without communication modules fall outside the red directive’s scope and do not require en 18031 certification.
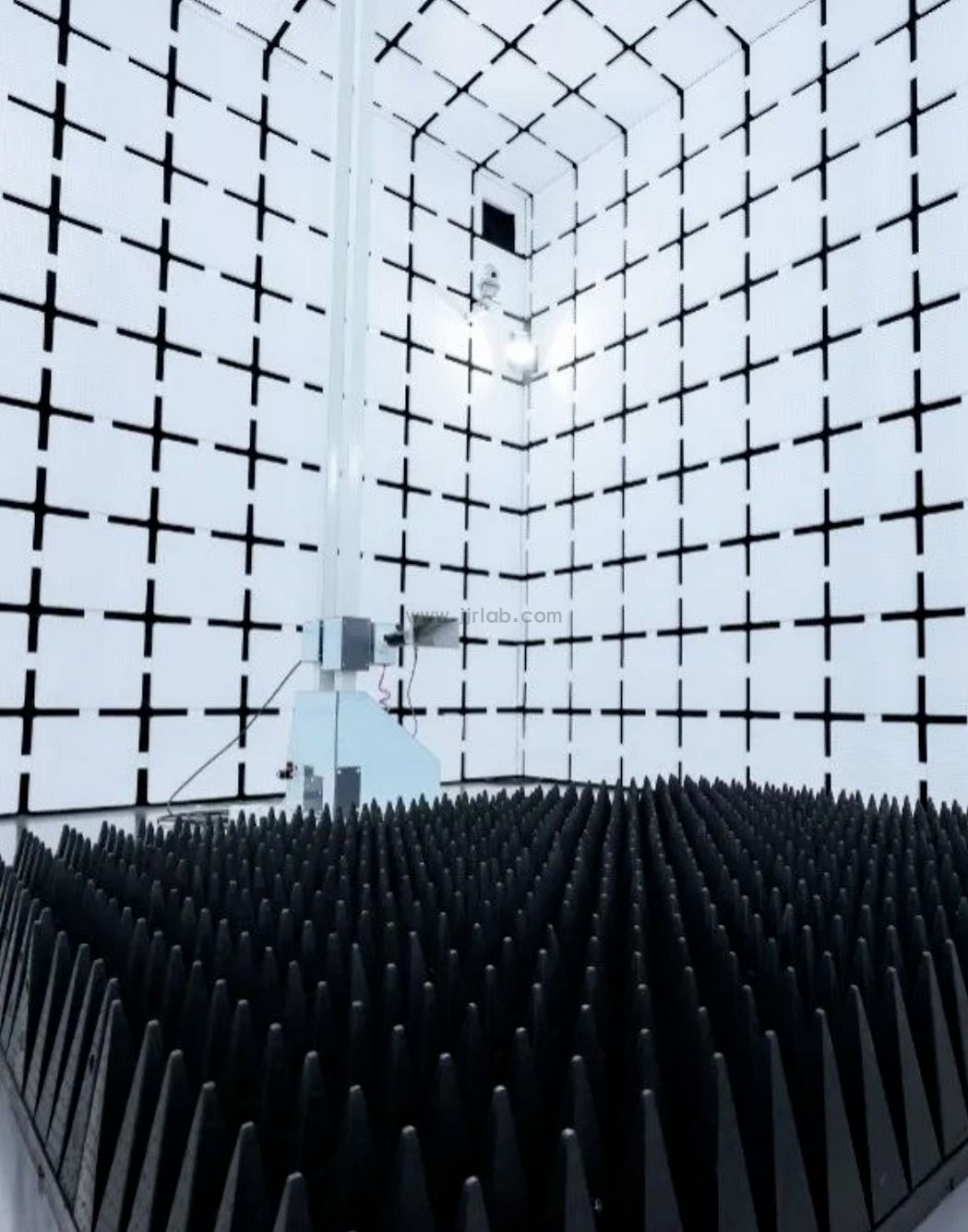
Certification Requirements for Six Types of Smart Locks
Type 1: Standard Lock (No Communication Module)
- Supports only local unlocking methods (PIN, fingerprint, face recognition).
- No Bluetooth/WiFi modules → No EN 18031 certification required.
- If biometric data is stored, it is recommended to follow EN 18031-2 encryption requirements (e.g., AES-256) for enhanced data security.
Type 2: Bluetooth Locks
- Mobile App Control
- Connects via smartphone Bluetooth.
- App processes accounts, unlock records, and data transfers.
- Requires EN 18031-1(network security) and EN 18031-2(privacy protection).
- Testing focus: Bluetooth encryption (TLS 1.3), app permission control, biometric local storage compliance.
- Bluetooth Remote Control
- Operated by standalone remote, no app, no network.
- No EN 18031-1 required.
- If biometric unlocking is supported → EN 18031-2required.
Type 3: WiFi Locks & Type 4: 4G/5G Locks
- Support remote control, temporary password sharing, video monitoring.
- Store biometric data.
- Must pass both EN 18031-1 and -2.
- High-risk test areas:
- Communication security (TLS 1.3 to prevent MITM attacks).
- Data storage (biometric data must remain local and encrypted; cloud upload prohibited).
- Firmware updates (security patches required within 90 daysof vulnerability discovery).
Type 5: Wired Locks (Ethernet Connection)
- Connect to LAN/Internet via Ethernet cable.
- No wireless modules → outside RED scope → No EN 18031 required.
- Still recommended to implement equivalent protections (e.g., brute-force resistance, encrypted storage).
Type 6: Zigbee Locks (Gateway-Dependent)
- Relies on Zigbee gateway for connectivity.
- Lock body and gateway may be sold separately.
- Best practice: certify lock + gateway as one systemunder EN 18031-1 and -2.
- If lock body alone is tested with gateway, the report only certifies the lock, leaving hidden risks.
- Strongly recommended: joint certificationof gateway + lock.
High-Risk Vulnerabilities and EN 18031 Protection Value
Smart locks face three primary threats, which EN 18031 directly addresses:
- Weak password brute-force attacks
- 61% of users set simple passwords (e.g., birthdays).
- Such passwords can be cracked in ~4 minutes.
- EN 18031 requires: ≥8-character alphanumeric passwords and a 5-attempt lockout mechanism.
- Biometric data leakage
- Some products upload unencrypted fingerprint templates to the cloud.
- Risk of identity spoofing.
- EN 18031 requires AES-256 local storage only, cloud upload prohibited.
- Communication hijacking
- Unencrypted Bluetooth commands may be intercepted.
- Full takeover possible in ~7 minutes.
- EN 18031 mandates TLS 1.3encryption to prevent MITM attacks.
Non-certified products face dual risks:
- Legal: After August 2025, uncertified products are banned from EU markets; sold units may be recalled and fined up to 4% of annual revenue.
- Security: 97% of uncertified locks have high-risk vulnerabilities; some can be hacked in 3 secondsdue to missing electromagnetic shielding.
Implementation Recommendations for Manufacturers
1. Accurate Classification to Avoid Over-Certification
- Standard/wired locks → no EN 18031.
- Bluetooth remote locks → only EN 18031-2.
- All other connected locks → EN 18031-1 & -2.
2. Zigbee Compliance Strategy
- Prioritize joint certification of lock body + gateway.
- Strengthen supply chain management (require pre-certification reports from gateway suppliers).
3. Technical Remediation Priorities
- Address critical risks first (e.g., disable remote unlocking unless NB-certified, deploy dynaMIC passwords).
- Cost optimization: use pre-certified secure chips (e.g., NXP SE050) to cut ~30% of test items.
With just one month left before August 2025 enforcement, manufacturers must immediately initiate vulnerability scans and documentation reviewsto ensure certification readiness and avoid market entry barriers.
Email:hello@jjrlab.com
Write your message here and send it to us
 European Toy Safety Standard EN 71-20:2025
European Toy Safety Standard EN 71-20:2025
 EN 18031 Certification for Connected Devices on Am
EN 18031 Certification for Connected Devices on Am
 Compliance Guide for Portable Batteries on Amazon
Compliance Guide for Portable Batteries on Amazon
 2026 EU SVHC Candidate List (253 Substances)
2026 EU SVHC Candidate List (253 Substances)
 LFGB Certification Cost and Timeline Guide
LFGB Certification Cost and Timeline Guide
 Bluetooth FCC Test Report
Bluetooth FCC Test Report
 Is FCC Testing Required?
Is FCC Testing Required?
 Where to Find FCC Test Reports
Where to Find FCC Test Reports
Leave us a message
24-hour online customer service at any time to respond, so that you worry!




