
Global Cyber Security Compliance for Connected Products
With the popULarization of Internet of Things (IoT) technology, "interconnection of everything" has become the norm, ranging from smart home cameras and wearable devices to industrial gateways. However, the attendant risks of cyber attacks have prompted major global markets to erect "digital firewalls". For export-oriented enterprises, cyber security is no longer an option but a mandatory threshold for accessing international markets.
This article sorts out the mainstream cyber security compliance requirements for connected products in Europe, America and the Asia-Pacific region.
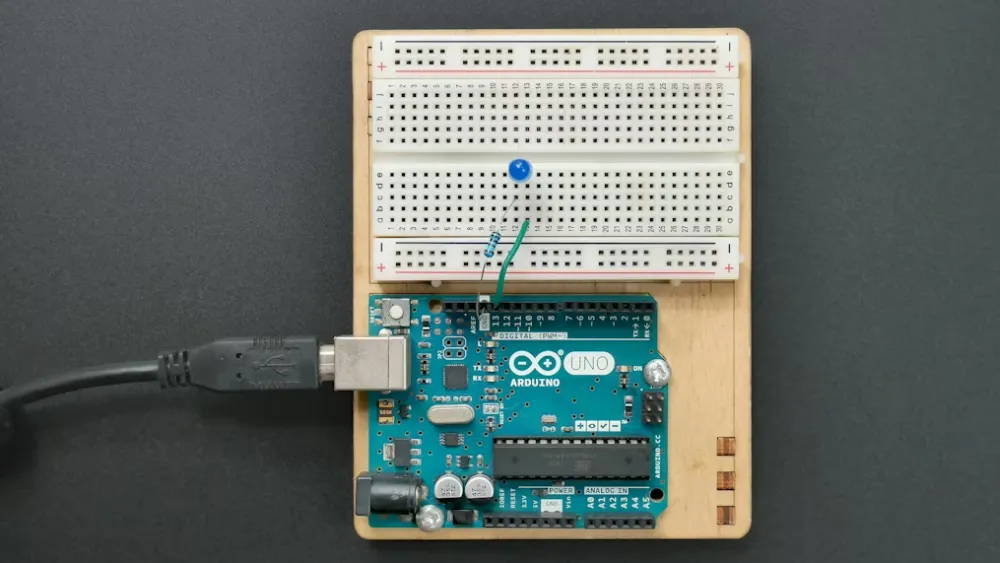
EU: Cyber Security Provisions of the RED Directive (Mandatory)
This is currently the regulation with the most far-REACHing impact on export enterprises. Pursuant to the implementing acts of the EU Radio Equipment Directive (RED), the provisions on cyber security (Article 3.3 d/e/f) have officially entered into force.
① Core Requirements: Devices must be capable of protecting networks, safeguarding personal data privacy, and preventing fraud.
② Technical Standards: The industry-recognized basis for assessment is currently the ETSI EN 303 645 standard, the world's first cyber security standard for consumer IoT.
③ Scope of Impact: It covers almost all wireless devices that communicate via the Internet, including smart home appliances, toys, and wearable devices.
④ Note: Devices that do not meet the RED cyber security requirements will be prohibited from entering the EU market for sale. Enterprises must incorporate the concept of "Security by Design" at the product definition stage during R&D.
UK: PSTI Act (Mandatory)
The UK Product Security and Telecommunications Infrastructure (PSTI) Act represents a fundamental regulatory framework for connected product security. Key mandatory requirements include:
① Ban on Universal Default Passwords: Devices shall not use generic factory-set passwords such as "admin" or "123456". They must adopt a "one device, one password" mechanism or force users to change the password upon first use.
② Vulnerability Disclosure Policy: Manufacturers must provide clear contact information for security researchers to report vulnerabilities.
③ Software Update Support Period: Consumers must be explicitly informed of the duration for which security updates will be provided for the product.
US: fcc Cyber Trust Mark and California Legislation
While the US market is dominated by state-level legislation (e.g., California SB-327), the implementation of unified federal-level certification is accelerating.
① FCC Cyber Trust Mark: This is a voluntary yet highly market-influential program. Obtaining the mark indicates that the product complies with high-standard cyber security requirements such as NIST IR 8425, which will significantly enhance the product's competitiveness among North American retailers (e.g., Amazon, Best Buy).
② Mandatory Trend: For devices involving critical infrastructure or government procurement, cyber security compliance has become a hard requirement.
Asia-Pacific Region: Singapore and Japan
1. Singapore Cyber Security Labelling Scheme (CLS)
The Cyber Security Labelling Scheme (CLS) launched by the Cyber Security Agency (CSA) of Singapore is divided into 4 levels. For consumer products such as smart home devices, Level 1 or Level 2 compliance is generally required, with a focus on default password management and software update mechanisms.
2. Japan Mic certification
The Ministry of Internal Affairs and Communications (MIC) of Japan has added security requirements for terminal devices in the telec certification (technical conformity assessment). Particularly for IoT devices, they are required to have access control functions to prevent unauthorized access and firmware update capabilities.
How Can Enterprises Respond? JJR Recommendations
Cyber security certification differs from traditional safety or emc testing, as it focuses more on software logic, encryption algorithms, and vulnerability management. For R&D and certification managers, we recommend the following:
1. Early Assessment: Do not consider cyber security only after the product is finalized, as modifying underlying code incurs extremely high costs.
2. Focus on Password Policies: "Weak passwords" are the most common cause of test failures; a sound password management mechanism must be established.
3. Document Preparation: Prepare vulnerability disclosure policy documents, software Bill of Materials (BOM) and security architecture documents in advance.
JJR has a professional technical team in the field of IoT cyber security. Based on standards such as ETSI EN 303 645 and NIST IR 8425, we can provide enterprises with one-stop technical services ranging from gap analysis and vulnerability scanning to final certification.
Email:hello@jjrlab.com
Write your message here and send it to us
 IEC 62471 Photobiological Safety of Lamps and Lamp
IEC 62471 Photobiological Safety of Lamps and Lamp
 New European Toy Standard EN 71-1:2026
New European Toy Standard EN 71-1:2026
 EN71 Series Standards Compliance February 13, 2026
EN71 Series Standards Compliance February 13, 2026
 European Toy Safety Standard EN 71-20:2025
European Toy Safety Standard EN 71-20:2025
 EN 18031 Certification for Connected Devices on Am
EN 18031 Certification for Connected Devices on Am
 Compliance Guide for Portable Batteries on Amazon
Compliance Guide for Portable Batteries on Amazon
 2026 EU SVHC Candidate List (253 Substances)
2026 EU SVHC Candidate List (253 Substances)
 LFGB Certification Cost and Timeline Guide
LFGB Certification Cost and Timeline Guide
Leave us a message
24-hour online customer service at any time to respond, so that you worry!




